RReductions
eductions
of informational entropy in continuous data froma networked of synchronized, true
random sequences generators in in
correspondencecorrelation with major world news events
R. D. Nelson,**,
D. I. Radin,†? R.
Shoup,‡? P.
Bancel§?
**?Department of Mechanical and Aerospace
Engineering, Princeton University, Princeton, New Jersey , 08544, USA
†?Institute of
Noetic Sciences, Petaluma, California, 94952, USA
‡??Boundary Institute, San JoseLos Altos, California,,
?????,
94024CA,
USA
§???????Paris, France
.........................................................................................................................................................
At some 40 sites
around the world, data are recorded from a network of true random number generators
attached to time-synchronized computers connected through the Internet. These generators produceing continuous, independent sequences
of random numbers that are collected into an archival database.[1] We examine this archive to determine the nature
and frequency of statistical aberrations in long-term, consistently generated
sequences. Samples taken during calibrations or resampled[2] at arbitrary timesthat
meet robust criteria for randomness in
samples taken during calibrations or resampled at arbitrary times.[3]
Duringrandomness, but during
certain pre-specified time
intervals predicted
predictively identified periods
there are, on average, significant departures
from
randomnessof distribution
parameters from random expectation indicating
structure in the data matrix.
These aberrations are
correlated with major events in the world and with a quantitative index of daily news
intensity, but
not with electromagnetic field fluctuations. This non-random behavior
of true random sources remains unexplained, and we suggest that other technical and
natural sources should be subjected to similar analysis. Here we describe focused analyses of
the data corresponding concentrating to on the disasters of September 11, 2001, ; the results indicate that reveal substantial
deviations from chance expectation in statistical parameters
and informational entropy, and further analyses show that these are not attributable
to identifiable physical interactions.
Research grade, hardware-based
trulyQuantum indeterminate, electronic random
number generators (RNG) with are designed with
protectionshielding from environmental influences such as
electromagnetic fields or fluctuations in temperature are designed to
produce cryptographically secure random sequences with near-maximal entropy.2, [4] Yet, under certain circumstances, such devices have shown surprising departures from theoretical
expectations. It is generally
assumed that no shielding is required against intense variations in the
perceptual or cognitive environment, in spite ofThere is
controversial but substantial evidence that distortions of statistical
distribution parameters may be correlated for unknown reasons with psychological statesconditions of importance to humans.[5], [6] To address this this putative physical-psychological
interaction in a rigorous
wayamong other issues, a long-term,
international collaboration was instituted in 1998 to develop a network to continuously
collect standardized RNG data continuously continuously over a period of years. The design required spatially distributed,
independent sources, employing secure data-collection and networking software
and high-quality RNG devices designed for serial computer interfacing.2, [7] The resulting matrix of random numbers can
be correlated with longitudinal data from many disciplines: cosmology, earth
sciences, meteorology, economics, even with and other metrics
of human activity. We find no overall relationship
with physical timeseries, but there is evidence that alterations in the
statistics of random data may be correlated with operationally defined measures
of human
attention to major world events.
On events.
On Sept. 11,
2001, our this world-spanning network of RNGs displayed
striking nonrandom
structure in several statistics. Though
it is the most extreme human event
case in the three-year database, the
apparent "imposed"
effect on the informational structure
is not unique to this day, but is found also in correspondence with other major
world events. The correlations are cleardemonstrable , but it is not obvious clear yet how they arise, or
whether there is some directan instrumental
link with the
world events or the intensely focused world attention. At this point we feel it is appropriate to
present an empirical description of methods and results,
to invite comment and independent analysis.
The project is fully described on a dedicated Web site that presents
results for a number of other examples of apparent structure where theoretically
there should be none under the null hypothesis, accumulated
over a period of three years.1 The Web site provides access to the original
data for researchers who wish to confirm our analyses or examine the data from
other perspectives.
Threeperspectives.
Three types of
electronic RNG devices are employed in the networkused. All use a quantum indeterminate level process as
the primary source of random events: thermal Johnson noise in resistors, or
quantum tunneling in solid state junctions.
They are designed for professional research and pass an extensive array
of standard
tests for randomness, based on calibration samples of a million 200-bit
trials.2 The devices are
shielded from biasing influences across most of the electromagnetic spectrum,
and utilize stable components and sophisticated circuit designs to protect
against environmental influences and component interaction or aging. In addition, the raw bit sequence is
subjected to a logical XOR against a known pattern of an equal number of 0 and
1 bits to guarantee an unbiased mean output.
Custom software collects data at a rate of one 200-bit trial per second
into time-stamped files on the local disk, with computer clocks synchronized to
standard
Internet timeservers. Secure data
packets are assembled and transmitted over the Internet to a server in
Princeton, NJ, for archiving in daily files containing the data for each node
for each second, registered in coordinated universal time coordinates
(UTC).
Standardized
analysis protocols used to examine the RNG outputs may be are used
to examine the
random data during periods corresponding to major news events such as the
disaster on Sept. 11.[8], [9] For example, in one analysis
the deviations of the 200-bit sums, or trial means, for each of
the individual nodes, can be are normalized
as
Zi
= (mi-μ?)/σ?m, and these Z-scores are combined
as Zs =Σ? Zi/N, where N is the number of nodes. Given these algebraic composite Zs representing each second,
a meaningful summary statistic for the period of interest is the sum of the
squared Zs, which is a χ?2-distributed
statistic quantity with degrees of freedom equal
to the number of seconds. This measure is responsive reflects to an excess of correlated deviation
among the nodes, and will tend to to be
large if the independent RNG devices are subjected to a common influence that
changes their output distributions in a parallel fashion.
On
Sept. 11, with 37 RNGs reporting, a trend to larger deviations began at
about 04:00 EDT early in the morning and continued for more
than 50
hours50
hours, until roughly noon on Sept. 13.
A "cumulative deviation" (cumdev)
plot, such as is used in process control engineering to identify changes in
monitored parameters, shows a striking departure from expectation of the χ?2
measure (Figure 1). The trace displays
an unexceptional random walk for several days preceding September 11 but then
changes dramatically. The aberrant
trend beginning just before the World Trade Center (WTC) attack is unique in in the
three-year database.:
a A trend with
this slope continuing for so long would happen by chance only once in about
2300 days. , and we find no other period of
similar deviation in the actual data. A
corresponding analysis
using
of a “clone” database with
pseudo-randomlyalgorithmically generated
clonereplicareplacement cell entries[10]
corresponding toof
the Sept. 11 dataset shows no unusual trend, which
rulesruling out analytical artifacts., and there
is no other period of similar deviation in the three-year database.
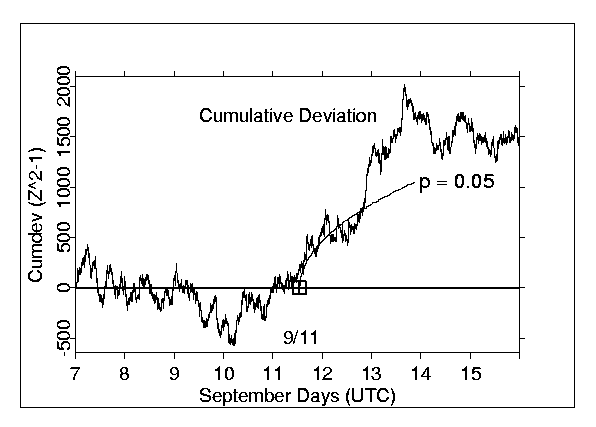
Figure 1: Cumulative deviation of χ?2
based on the composite meanshift across RNG devices for each second, Sept. 7
through 1315, 2001. Day boundaries are in UTC and t The
terrorist attacks are is marked with a
boxrectangle
on the line of zero deviation. A
parabolic curve beginning at the time of the attacks provides a 5% probability
comparison.s A segment of
the parabolic envelope of 95% confidence with origin at 08:45 EDT (12:45 UTC), provides
scale for the persistent trend of the random walk.
Low
pass filtering with windows of 10 to 60 minutes shows substantial, persistent
increases in this measure in extended bursts from approximately 04:00 to 05:00,
08:30 to 12:00, and 12:45 to 14:30 EDTD.
T. Spikes in the unfiltered,
one-second composite deviations indicate an excess of inter-node
correlations. To test more generally
for intercorrelations of the independent nodes, all possible correlations among
the RNGs were calculated for each day's data over a period of a year, and each
correlation then was transformed
to a Fisher Z-score.
The day with the largest value on this mean intercorrelation measure is Sept. 11,
and it differs significantly from the mean of the
distribution for all days from Dec. 1, 2000 to Dec. 31, 2001, t = 3.67 (p = 0.00012).
The aberrant behavior of the
data array
on Sept. 11 is
more sharply The defined in the variance (σ2) across the
independent RNG devices. also exhibits unusual structure, as
shown in Figure 2. There shows is a
notable structure,
with change a major departure from random fluctuation beginning
about four hours before the first attack.
At that time, the variance increases over expectation by a striking
amount, and it
continues to exhibit excess until about 11:00 EDT,
shortly after the fall of the second WTC tower. Then the variance then undergoes
a precipitous decrease that persists for several hours until about 18:00
EDT. Over the course of approximately
seven hours from 06:30 to 13:3011:00 to 18:00,
the change from maximum to minimum maximum to minimum cumulative
deviation is equivalent to 6.8.5 standard errors (σm)sigma. Monte Carlo analysis determines that such an
extreme monotonic trend in less than 8 hours would occur with a chance
probability of approximately less than 0.002. Similarly, aA bootstrap permutation
analysis,
reordering the actual data, yields an similar
estimate of p = 0.0048
0009
for the peak excursion, based on 10,000 iterations. For the Sept. 11 clone data the corresponding estimate is p = 0.756. Figure 2 also shows the pseudo-random clone
data in a visual comparison. There are
no similar, long-lasting trends in these "control" data..
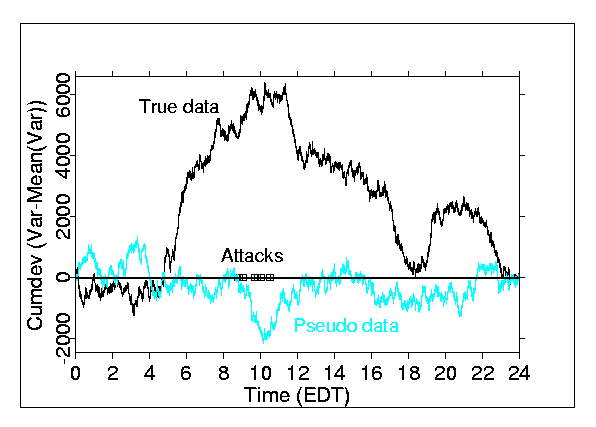
Figure 2: Cumulative deviation of variance (σ2variance ) across RNG devices, relative to the empirical mean value, across
RNG devices for each second, on
Sept. 11, 2001. The truly random data
from the network are contrasted with a pseudo-random “clone” dataset computed
for the same array of data elements processed with the same algorithms. TAxis labeling is in
EDT; times of the terrorist attacks are indicated with rectangles
boxes
on the zero line.
Figure
2 also shows the
pseudo-random cloned data
for Sept. 11 for comparison; there
are no similar, long-lasting trends in these "control" data. To assess the
generality of the variance effects in the actual data, we S separateding
the RNGs into subsets on the basis of their location, as well as by random
assignment. The results indicated that shows that similar aberrant
trends are exhibited generally across the independent devices. Computation of a complexity measure used to
reduce dimensionality in neurophysiological data shows that a parameter closely
related to variance is by far the largest contributor in a standard
three-parameter representation.[11] To
aid in visualizing the variance excursions over long-extended periods, low-pass
filtering with smoothing windows of one to six hours were applied to data from
July through October 2001, and a six-hour window was applied to all days for a
year. The results clearly show that
Sept. 11 is unique: no aberration of comparable magnitude occurred on any other
day from Dec. 2000 to Nov. 2001.
The
next question is whether there is are any temporal correlations in the datacross-temporal linkage. The sequential autocorrelation function is
generally used as a check for independence of successive events. In the Sept. 11 data
we discoverThere are no short lag time anomalies
in the autocorrelation function of the composite meanshift or
variance on Sept.
11 for short lag times;
the data appear to be independent on a time scale of seconds. The aAutocorrelation function
is, of course, also sensitive to extended excursions, and to
cyclic or sustained fluctuations. Figure
3 shows the autocorrelation function of the composite variance during the 24-hour
UTC window
for Sept 11,
using 5-second blocks. The function was computed via Fourier transform for as a
function of lag,lags from 1 second up to fourthree
hours. , during
It
shows a
strong departure from expectation, witha 14-hour
window from 04:00 to 18:00. This period
was selected to include
the clusters of
aberrant data that appear to drive the deviations of distribution parameters. The
autocorrelation that
is consistently positive and highly significant for lags up to about one
hour, thenslightly less it drops slightly over
the second hour,
after which it drops to the expectation level. The deviation is so persistent hat the
trace penetrates a 10-6 probability threshold, implying a
probability less than 0.001. The return to zero
correlation fFor lag times greater than two hours it
drops to the expectation level of zero, implying implies that the
deviant periods driving theis sequential a autocorrelation temporal
linkage were on the order of one to two hours longin length.. The overall
probability of such a large accumulation
of excess autocorrelations in this
14-hour window is on the order of 1 part in 109.
[measured how?] Windowing the full
24-hour day yields a probability of 10-5. For comparison, the figure includes traces showing the same
computations for ten other days from September 5 to 15, all of which fall
within a 95% confidence envelope. These
results imply a reduction of informational entropy in the nominally random data
during and around the time of the Sept. 11 disaster.
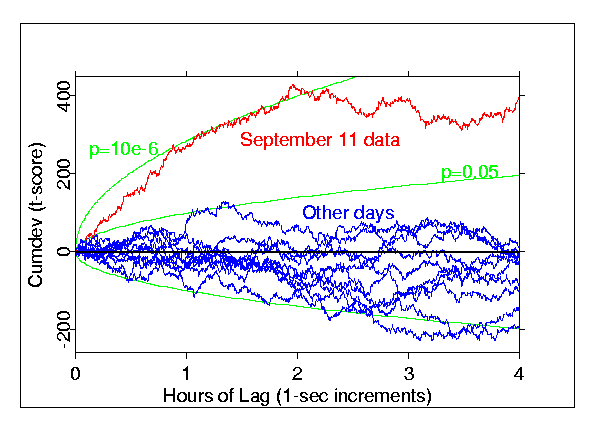
Figure 3: Autocorrelation of GCP scores for Sept. 11,
2001, contrasted with the same calculation for 10 surrounding days. The variance of the trial scores across RNGs
was converted to an approximate Z-score
in
5for
each -second blocks
for the 24-hour UTC day. The
autocorrelation function for this time series was computed over lags of 5
sec to 3up to four hours. Deviations from theoretical expectation for this normalized function
are plotted here as a cumulative trace, summing the squared,
normalized correlation coefficient, less its expectation.. Excess correlation is evident for lags up to
2 hours, and the maximum cumulative deviation has a chance
probability of 10-5. At lags
longer than 2 hours, the autocorrelation reverts to normal.
This overview of the evidence for structure in a
large array of nominally random data collected on Sept. 11, 2001 should be
placed in the context of the long-term research project, but space does not
permit a detailed presentation of the full corpus. In brief, Tthere
have been over 95 formal analyses of data associated with world news events
such as the African embassy bombings in 1998, four New Year transitions,
several natural disasters including earthquakes and floods, Internet-promoted large-scale
meditation eventspeace meditations, and political events
with international impact.
The results show the statistical variations
expected of low signal- to- noise measures, but
about two-thirds of the cases have a positive outcome relative with
respect to the null hypothesis, and 21% are independently
significant at or beyond the 5% level. The
composite probability that chance fluctuation can account for the total
deviation from expectation across these focused analyses 95 replications of
this experiment is less than one part in a 107. Based on the intercorrelation measure
described earlier, these major news events tend to occur on
days with significantly higher intercorrelation among the RNGs. To assess this relationship more generally,
an objective metric was constructed based on an independent survey of news
events.[12] The count of characters in the summaries of
news items was taken to represent the news intensity. Over the one-year period from Dec. 2000 through Nov. 2001, this
measure, though
diffuse, is correlated with daily mean intercorrelations of the RNG data
at r = 0.15, t (362 df) = 2.94, p = 0.002.[13]
Figure 4: Correlation between daily news metric and
daily RNG intercorrelation values.
Sept. 11, 2001 is associated with a news metric value of 398 in this
graph.
Alternative
explanations for these departures of nominally random data from their expected
values must be addressed before we seriously consider the anomalies to reflect
human reactions to events such as the Sept. 11 disaster. The electromagnetic spectrum is an obvious
candidate. Could mMajor changes in
the electrical supply grid that were caused by the destruction, or and there was an enormous
surges in cell-phone activity, or and an unusualan coherence
increase in radio and television broadcasting coherence
somehow have affected the RNG network?. Because the devices are distributed around
the world, their average distanceseparation from
the physical disruption was on the order ovaries greatly (fmean distance,
6400 Km),
but the effects
is
described
above are broadly distributed across the network. The appearance of strong deviations well prior to the attacks presents yet another
conundrum,
but it is inconsistent with EM field explanations. More
definitive is the instrument design, which includes physical shielding from EM interference down
to about 1 Hz, and in addition, includes a logic stage that literally
eliminates first-order biasing from electromagnetic, environmental, or other
physical causes. These indications are
confirmed by analytical results.
Empirical computations based on RNG outputs according to local time the timeseries of daily intercorrelations show
that there is no correspondence with expected diurnal variations in the power grid
and no diurnal or other known cyclic
patterning.10 12 We can find no evidence that physical
influences arising from the extreme conditions of Sept. 11 were responsible for
the structure found in these RNG data.
ODefinitive answers
to the questions posed by these findings will not be easy to find because our
analyses point to anomalous departures from expectation in nominally random
data that are related, de facto, to
global events of great importance to human beings. The LocatingTo identify the source
of the deviations
we must account for excess inter-node correlations, persistent changes in
composite variance, and long-term autocorrelations, all indicating significant
alteration in the informational entropy of the data array. The aberrations in the RNG data
are correlated with objective measures of news intensity, but not with any
likely physical variables. Although the
observations reported here are apparently
quite unconventional, the evidence is strong sufficiently compelling enough
to justify deeper investigation, and we invite other researchers
to examine the data in a broad-based search for better understanding. We would be grateful for access to other
continuously recorded, nominally random data sequences that can be examined for
aberrations similar to those reported here.
Acknowledgements
This work was
supported in part by the Institute of Noetic Sciences, with financial
contributions from numerous individuals.
Computing and technical support were provided by the Princeton
Engineering Anomalies Research program, Princeton University.
Correspondence
and requests for materials should be addressed to R.N. (email:
rdnelson@princeton.edu.)